Major Cyberattacks and Data Breaches
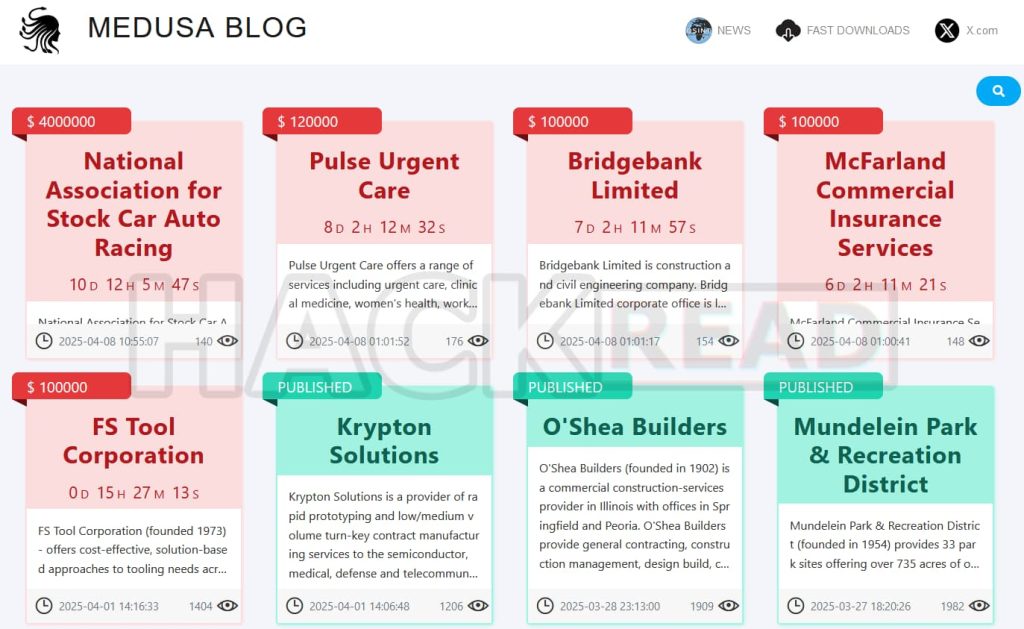
Medusa Ransomware’s dark web leak site (Credit: Hackread.com)
Medusa Ransomware Targets NASCAR
On April 8, 2025, the Medusa ransomware gang claimed responsibility for attacking NASCAR, demanding a $4 million ransom. Hackers leaked 37 files containing internal data such as raceway maps, staff contact info, and credentials. If confirmed, this would mark the second breach of NASCAR this season. Read more
Healthcare Lab Breach: 1.6M Records Compromised
Laboratory Services Cooperative (LSC) disclosed a breach affecting 1.6 million individuals. Attackers accessed personal identifiers (e.g., SSNs, passport numbers) and health data. Though detected in October 2024, the breach was disclosed only now. More details
Email Compromise of U.S. Bank Regulators
Hackers accessed 150,000 emails from 103 U.S. bank regulators at the Treasury’s Office of the Comptroller of the Currency between May 2023 and Feb 2025. The breach was reported on April 8 and labeled a “major incident.” Report
Oracle Breach and Alleged Cover-Up
Oracle admitted a breach involving a legacy system, exposing customer credentials. A class-action lawsuit filed on April 7 claims a separate March 2025 breach affected 6 million records across 140,000 Oracle Cloud tenants. Full story
Other Disclosures
- Europcar reported theft of source code and customer data (200k+ records).
- State Bar of Texas exposed legal documents in a ransomware attack.
- Port of Seattle revealed a Rhysida ransomware attack from Aug 2024 affecting 90,000 individuals. Overview
Major Vulnerabilities and Patches

Microsoft Patch Tuesday (April 8, 2025)
Microsoft patched 134 vulnerabilities, including the actively exploited CVE-2025-29824, a CLFS driver bug used in ransomware attacks. Malware known as “PipeMagic” exploited it for SYSTEM-level access. Patch info
Android Zero-Days
Google fixed two zero-day vulnerabilities on April 10, including:
- CVE-2024-53197, linked to Cellebrite exploitation.
- CVE-2024-53150, a kernel bug found by Google’s TAG. Details
Fortinet FortiSwitch Vulnerability
CVE-2024-48887, a critical flaw allowing admin password changes without verification, was found in FortiSwitch devices. Fortinet issued patches and mitigation advice. More info
Firefox 137 Security Update
Mozilla patched CVE-2025-3028 and CVE-2025-3030 — both critical memory safety issues — in Firefox v.137. These bugs could allow remote code execution. Update announcement
Other Notable Vulnerabilities
- WinRAR CVE-2025-31334: Bypasses “Mark of the Web” security. Details
- ESET CVE-2024-11859: Used by ToddyCat APT to load malicious DLLs. Read more
- FortiGate VPN Abuse: Attackers created symlinks to retain access even after patching.
Government and Industry Responses
UK Ruling on Apple Backdoor Case
On April 11, the UK’s Investigatory Powers Tribunal ruled that details of a secret attempt to force Apple to install backdoors must be partially disclosed. Apple maintains it has never, and will never, create backdoors. Coverage
Irish DPC Investigates X’s AI Data Use
Ireland’s DPC launched an investigation into X (formerly Twitter) over using public posts to train its AI, potentially violating GDPR. The case centers on transparency and prior consent. Full report.
OpenAI Adds Watermarking to Images
OpenAI began watermarking AI-generated images in ChatGPT’s free tier. The move aims to address concerns over misuse, especially regarding copyrighted styles. More
U.S. Seizes $8.2M from Romance Scam Networks
U.S. authorities recovered $8.2 million tied to romance scams that exploited dating apps and crypto platforms. Blockchain analysis enabled tracking through DeFi and exchange layers. Details
Tax-Themed Phishing Surge
Microsoft and U.S. agencies warned about tax-season phishing campaigns, with PDFs containing malware or fake tax portals. Victims were redirected to fake DocuSign pages. Warning
Miscellaneous
On April 14, 2025, Florian Roth, creator of YARA Forge, announced the removal of Elastic Security’s YARA rules due to license restrictions. Elastic License v2 prohibits hosted services from offering the rules, conflicting with YARA Forge’s mission. Roth emphasized the need for open licensing and recommended alternatives like the Detection Rule License (DRL).
What is YARA Forge?
YARA Forge is a curated platform for YARA rules used in malware detection. It provides:
- Core Set: Low false positives
- Extended Set: Broader coverage
- Full Set: Comprehensive hunting rules
The Elastic rules removal reignited debate over restrictive licenses and the need for community-friendly rule-sharing practices.More
Conclusion
This week’s developments—ransomware attacks, espionage breaches, patch releases, regulatory actions, and license disputes—underscore the complexity of today’s cybersecurity landscape. Organizations must:
- Patch vulnerabilities promptly
- Monitor breach disclosures
- Evaluate legal implications of third-party tools
- Support open, collaborative initiatives like YARA Forge
Sources
This summary includes references from:
