Introduction
CVE-2020-1472, also known as “Zerologon”, is a critical vulnerability that allows an unauthenticated attacker to gain domain administrator access to any given, vulnerable Domain Controller (DC). This is due to the incorrect use of an AES mode of operation, which allows anyone to spoof the identity of any computer account and set an empty password for that account in the domain. This vulnerability is rated with the highest possible CVSS score of 10.0 (critical). All versions of the Windows Server Netlogon Remote Protocol are affected, and the setup phase for the attack remains straightforward. The only requirement is the ability to set up a TCP connection with a vulnerable DC.
Presenting the Netlogon Protocol
What is the Netlogon Protocol Used For?
The Netlogon Protocol handles machine and user authentication, authentication of NTP (Network Time Protocol) responses, and allows a computer to update its password in a domain. This last capability is of particular interest to attackers aiming to compromise users or entire domains.
Understanding the Netlogon Handshake
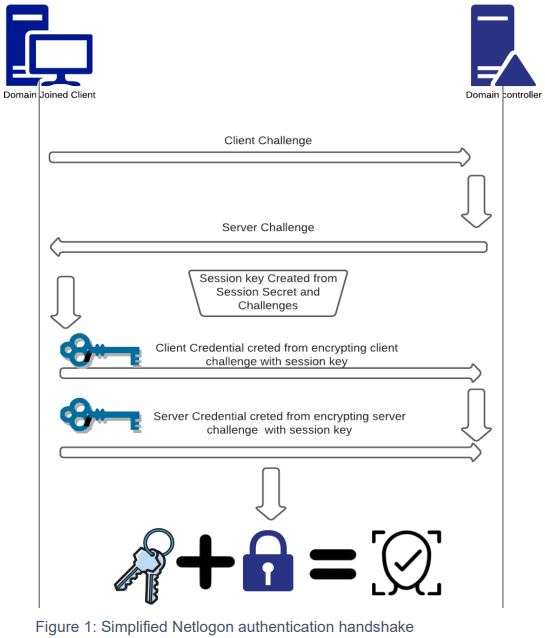
The client initiates the handshake by sending an 8-byte arbitrary value, the ClientChallenge. The server responds with the ServerChallenge. These challenges, or “nonces”, are used to derive a session key through a key derivation function (KDF). The client generates a ClientCredential using the session key. The server verifies this by recomputing the value. If it matches, the client is authenticated. The server then sends a ServerCredential for mutual authentication. The parties may agree to encrypt and/or sign subsequent messages.
What Causes the Vulnerability?
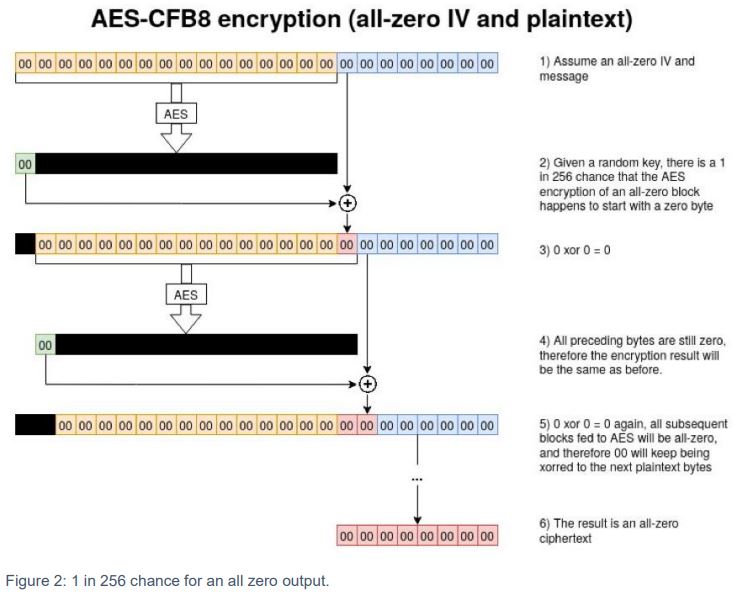
The flaw lies in how ClientCredential and ServerCredential values are computed via the ComputeNetlogonCredential Function. This uses AES-CFB8, a mode of operation for AES. AES-CFB8 should use a random Initialization Vector (IV) for each session, but Netlogon implementation uses a fixed IV of 16 zero bytes. This violation allows for a 1 in 256 chance that an all-zero input results in an all-zero output.
This enables brute-force attacks using all-zero authentication packets. Eventually, the all-zero iteration in AES-CFB8 is hit, allowing successful authentication.
How Does the Exploitation Work?
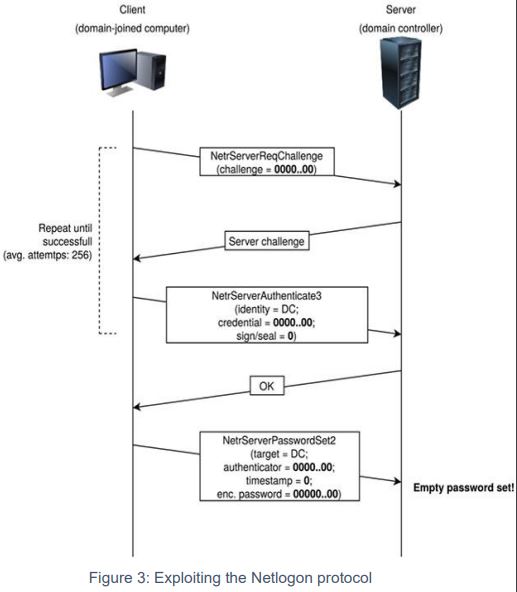
Step 1: Initiation
The attacker sends a specially crafted Netlogon message to the domain controller.
Step 2: Malicious Netlogon Messages
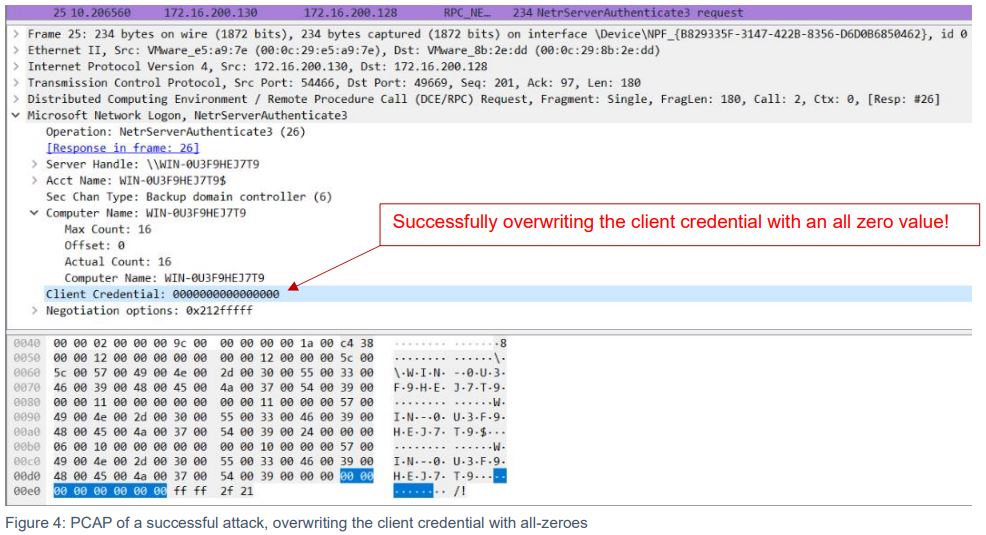
The attacker sends around 256 malicious Netlogon messages with empty plaintext fields using AES-CFB8. Due to the fixed IV, the attacker can compute the ciphertext without knowing the AES key.
Step 3: Authentication Bypass
The attacker exploits the all-zero ciphertext validation flaw to impersonate the domain controller.
Step 4: Change a Computer’s AD Password
The attacker changes the domain controller’s computer password to an empty value.
Step 5: Privilege Escalation
With the password set to empty, the attacker can establish a secure channel and gain administrative access to the domain.
Impact
- Complete Domain Compromise: Access to all critical resources and sensitive information.
- Privilege Escalation: Gain control over high-privilege systems.
- Spread of Malware: Distribute malware across the network.
Defending Against Zerologon
How to Mitigate the Vulnerability
Microsoft released a patch in their August 2020 security update. Apply the patch to mitigate the risks. Additional steps:
- Enforce secure RPC communication.
- Monitor network traffic for suspicious Netlogon activity.
- Use enhanced features like Microsoft’s Domain Controller Enforcement Mode.
Artifacts to be Observed
Detectable artifacts include:
- Windows Event ID 4742: “A computer account was changed.”
- Windows Event ID 4672: “Special privileges assigned to new logon.”
Event 4742 is uncommon but not unique to attacks. Event 4672 relates to privilege escalation, not the core exploit. It’s recommended to monitor for unusual traffic spikes as well.
How Can I Check if You Are Vulnerable?
Use the test-tool published by Secura to check for Zerologon vulnerability.
Summary
CVE-2020-1472, or Zerologon, posed a severe threat to numerous networks due to its simplicity and the devastating impact of a successful attack. With just TCP access to a vulnerable domain controller, an attacker could compromise the domain.
This vulnerability highlighted how minor implementation errors can break an otherwise secure system. Regular updates and timely patching are essential for maintaining system security.
