Introduction
On October 4th, Atlassian disclosed a zero-day vulnerability affecting Confluence Server and Confluence Data Center, which allows a remote, unauthenticated user to create administrator accounts on the vulnerable Confluence instance. At the time of disclosure, the vulnerability was ongoingly being exploited by a Nation-State-Threat-Actor, with attacks dating back as early as September 14th, as stated in this report from Microsoft.
The vulnerability tracked as CVE-2023-22515 received the highest possible CVSS score of 10.0, ranking it as ‘critical’. Initially, the attack vector was rated as Privilege Escalation, but soon after Atlassian updated it to a Broken Access Control.
An attacker can exploit CVE-2023-22515 to reactivate the setup phase of the Confluence instance; he then leverages this to create an additional administrator account with his own credentials. No prior knowledge is needed to execute this attack.
Presenting CVE-2023-22515 Attack Stages
Stage 1: Change the completion status of the configuration to ‘false’
When an attacker tries to access the setup page for any given Confluence page (https://<confluence-domain>.atlassian.net/setup), he will get the following message:
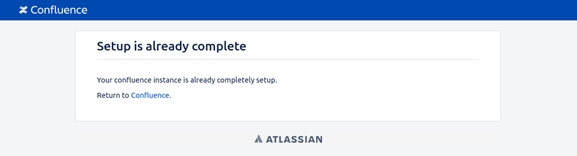
So, in order to start the attack, the attacker needs to send a GET request containing the following payload to the /server-info.action endpoint:
bootstrapStatusProvider.applicationConfig.setupComplete=false
For a detailed explanation, refer to this blog article from Qualys.
After successful execution of the payload, the server will respond with a ‘success’ message confirming it is operational and that the configuration phase is recognized as uncomplete.

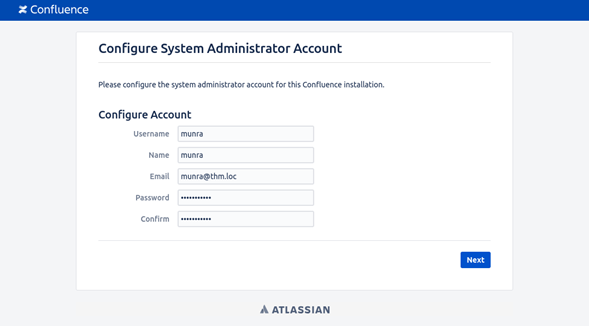
Stage 2: Accessing the ‘setupadministrator’ endpoint
Now that the setup phase status is marked as incomplete, the next step for the attacker is to access the setupadministrator endpoint:
http://10.10.41.49:8090/setup/setupadministrator-start.action
Trying this directly, the attacker will receive a 403 Forbidden response. To bypass this, the attacker must add the following header to the request:
X-Atlassian-Token: no-check
Including this header, the attacker is now able to create a new administrator account.
Stage 3: Finishing the Setup
To exit the setup, the attacker proceeds with another POST request to the /setup/finishsetup.action endpoint. The attacker can now log in with the newly created administrator account.
The GitHub page provides an automated exploit. Use it ethically and only with permission.
To test the exploit in a safe environment, visit the TryHackMe room.
Impact
By having full access to all resources on Confluence, an attacker can modify, delete, and exfiltrate data, impacting the Confidentiality, Integrity, and Availability of the data. It is highly recommended to patch the vulnerable versions as soon as possible.
Defending Against CVE-2023-22515
Affected Versions
Atlassian reported the following versions of Confluence Data Center and Server as vulnerable:
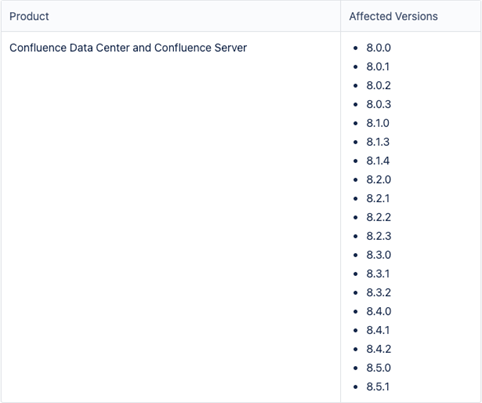
(Source: Atlassian)
Versions prior to 8.0 are not affected. Cloud Instances hosted by Atlassian are not vulnerable.
How to Mitigate the Vulnerability?
Permanent Mitigation
Affected organizations should upgrade to one of the following fixed versions (or later):
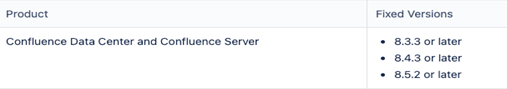
(Source: Atlassian)
Note: Upgrading an already compromised instance will not remove the attacker’s access. Isolate the server and contact Atlassian Support.
Temporary Solution
If an immediate upgrade is not possible, block access to the /setup/ endpoint. Add the following constraint inside the <web-app> tag in /confluence/WEB-INF/web.xml:
<security-constraint>
<web-resource-collection>
<url-pattern>/setup/*</url-pattern>
<http-method-omission>*</http-method-omission>
</web-resource-collection>
<auth-constraint />
</security-constraint>
Indicators of Compromise (IOCs)
- Unknown members in the
confluence-administratorsgroup - Unexpected newly created user accounts
- Unknown installed plugins
- Requests to
/setup/*actionin network access logs - Presence of
/setup/setupadministrator.actionin exception messages inatlassian-confluence-security.log
Datadog Security Labs released a list of IPs likely associated with compromise.
Summary
Confluence CVE-2023-22515 allows remote, unauthenticated users to create administrator accounts on non-Atlassian-hosted Confluence sites. It is a critical zero-day vulnerability, already being exploited at the time of disclosure. Organizations are urged to patch affected systems immediately and implement strong backup and response processes.
