Introduction
What is this new CVE?
This vulnerability, charmingly nicknamed “Looney Tunables,” affects version 2.34 of the GNU C library (GLIBC). It was discovered on October 3rd of this year. It is a buffer overflow impacting the processing of the environment variable GLIBC_TUNABLES, in the dynamic loader ld.so. This vulnerability enables a local attacker to exploit specially crafted GLIBC_TUNABLES environment variables when executing binaries with SUID permissions, then run code with elevated privileges.
This is a high-risk vulnerability due to its potential for elevating privileges and its broad impact across various devices. Indeed, numerous Linux distributions, including Fedora, Ubuntu, and Debian, are susceptible to this vulnerability. However, certain distributions such as Alpine Linux remain unaffected since they employ MUSL LIBC rather than GLIBC.
What is a buffer overflow?
A buffer overflow is a critical software vulnerability that occurs when a program writes more data into a designated storage area (buffer) in memory than it can hold. This excess data can spill over into adjacent memory locations, potentially corrupting or overwriting important information or code. In the worst cases, malicious actors can exploit buffer overflows to inject and execute arbitrary code, gaining unauthorized access or control over a system. Buffer overflows are a significant security concern and are typically addressed through secure coding practices, bounds checking, and other protective measures to prevent potential exploits.
What is the dynamic loader ld.so and GLIBC_TUNABLES?
The ld.so program collaborates with ld-linux.so to locate and load the necessary shared libraries for a program, ready it for execution, and then execute the program.
The environment variable GLIBC_TUNABLES is a feature in the GNU C library that enables the modification of the runtime library behavior.
Demonstration
Setting up the VM
I utilized an Ubuntu 22.04.3 ISO to perform the installation on my virtual machine, without internet connection. By doing this, I ensured that the GLIBC remained not updated. All other installation settings were left at their default values.
Proof-of-Concept
After the VM installation is complete, I can execute the Proof-of-Concept command as specified in the Qualys Security Advisory.
Let’s explain this command first:
env -i: Run the command with an empty environment.GLIBC_TUNABLES=glibc.malloc.mxfast=glibc.malloc.mxfast=A: Assign this value to the GLIBC_TUNABLES environment variable.Z=\printf ‘%08192x’ 1``: Assign to the environment variable Z the command printf that generates a long string of 8192 “1”. (That’s the buffer overflow.)/usr/bin/su --help: The command executed, just shows the help message of the su command.
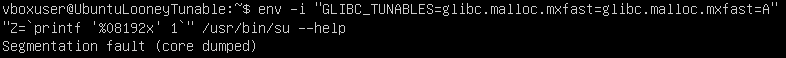
In this scenario, when we receive the message “Segmentation fault (core dumped)”, it signifies our effective memory injection, confirming the device’s vulnerability. Although we’ve injected only a few “1s” in this instance, it demonstrates our capability to inject more malicious code if desired.
Let’s update!
Now, we are going to fix it with a good old: apt update && apt upgrade
GLIBC is now up to date and if we enter the same command as before, we receive a different message. The system is no longer vulnerable!
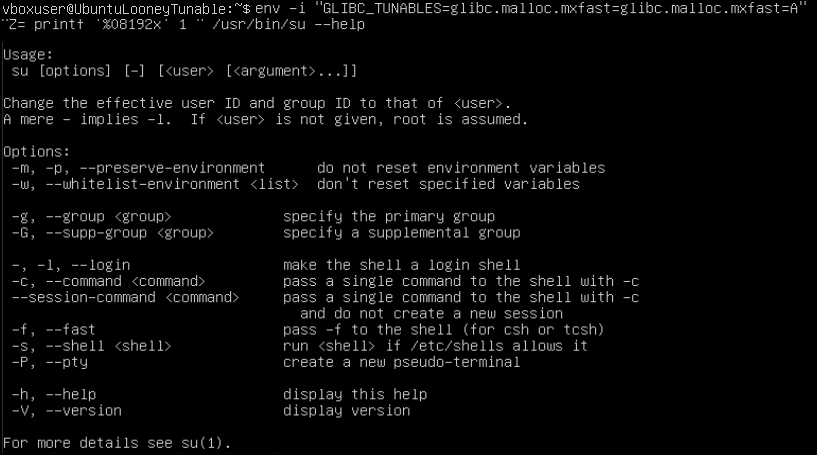
If you want to update just the GLIBC package, you can do so with this command: apt install libc6
How to prevent this in a SOC
If you are using Microsoft Defender for Endpoint, you will find it in the Vulnerability section.
If not, you can check the version of GLIBC with this command: /lib/x86_64-linux-gnu/libc.so.6
If the version is 2.34, watch out! You may be vulnerable to Looney Tunables. To be sure, you can enter the Proof-of-Concept command seen above.
Conclusion
In summary, we’ve established that this CVE affects GLIBC version 2.34, impacting a multitude of Linux distributions. This vulnerability allows the attacker to inject and execute code with root privilege. Fortunately, patching it is relatively straightforward, thanks to the package manager. All it takes is a system upgrade. However, it’s crucial to exercise caution, as many Debian/Ubuntu servers may not receive regular updates, making this vulnerability a significant concern.
The “Looney Tunables” vulnerability serves as a vivid example of the constantly evolving threat landscape that security experts grapple with. Nevertheless, it also underscores the unwavering commitment and diligence of the open-source community, tirelessly engaged in identifying and remedying such vulnerabilities.
