INTRODUCTION
In an era where online security and privacy are paramount concerns, the recent introduction of Encrypted Client Hello (ECH) in TLS 1.3, which entered the production phase in October 2023, represents a remarkable leap forward. ECH is a groundbreaking innovation that aims to revolutionize the way we initiate secure connections on the internet.
By concealing the client’s destination, ECH promises to provide enhanced privacy. As we delve into the behavior of ECH, we will discover both its potential benefits and the complex issues it introduces.
The Evolution of Privacy in TLS: The Encrypted Client Hello
In today’s ever-changing digital landscape, data privacy and security take center stage. A significant milestone in this domain is the integration of the Encrypted Client Hello (ECH) within the Transport Layer Security (TLS) protocol. To appreciate its significance, let’s explore the evolution of TLS and the privacy concerns that led to ECH.
Before TLS 1.2, numerous details exchanged during TLS session initiation remained unencrypted, exposing sensitive data to potential interception. Concurrently, Edward Snowden’s revelations about mass surveillance triggered a response from the Internet Engineering Task Force (IETF), aiming to enhance TLS security.
TLS 1.3 played a pivotal role by encrypting X.509 certificates, strengthening data privacy. Additional protocols like DNS-over-HTTPS (DoH), DNS-over-TLS (DoT), and DNS-over-QUIC (DoQ) emerged to secure client access to DNS resolvers. However, a critical vulnerability persisted: the Server Name Indication (SNI) shared during the Client Hello.
SNI is essential for TLS connection negotiation, informing the server about the client’s intended website, allowing the selection of the appropriate certificate. Yet, the challenge lies in the fact that TLS and HTTP operate independently. When a server hosts multiple websites on a single IP address, determining the right site becomes problematic. SNI steps in by indicating the client’s desired website at the session’s outset.
Establishing encrypted communication requires a shared secret. TLS starts asymmetrically, meaning it must establish unencrypted communication initially. It commences by introducing itself to the server with a Client Hello, containing various parameters like SNI, ALPN (Application-Layer Protocol Negotiation), and other vital data. The challenge here is to protect this information during the initial negotiation.
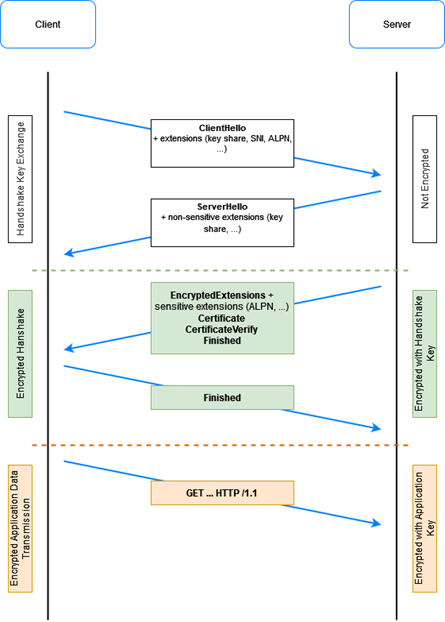
The concept of encrypting SNI gave rise to the Encrypted SNI (ESNI) draft. However, it became evident that encrypting the entire Client Hello, encompassing crucial parameters such as ALPN, was a more prudent approach. Thus, the Encrypted Client Hello, also known as ESNI in the literature, was conceived.
ECH: How it works
Now that we’ve set the stage for the Encrypted Client Hello (ECH), let’s delve deeper into how this innovation operates.
When the encryption process begins, concealing the client’s destination is crucial. Yet, the challenge emerges in how to encrypt communication meant to be the initiator of the encryption session itself. This is where the concept of nesting comes into play. The primary unencrypted ClientHello is referred to as ClientHelloOuter and does not contain sensible information. However, nested within ClientHelloOuter is the actual ClientHello, known as ClientHelloInner. The question then arises: how can we encrypt this ClientHelloInner from scratch?
To answer this question, we need to introduce an ingenious concept called the Client Facing Server (CFS). It is used to hide the client’s primary destination. It operates by concealing numerous servers behind it, creating a vast layer of anonymity. While this concept might sound complex, infrastructure like Content Distribution Networks (CDNs), exemplified by CloudFlare, already provides similar services.
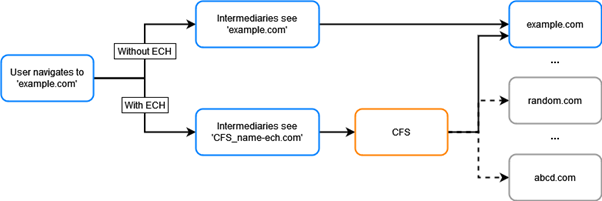
Then, hybrid cryptography comes into play. The CFS utilizes this cryptography to generate a configuration vector containing the public key required for the client’s destination over the next 48 hours. But how does the client obtain this information? Here’s where a modification in DNS operation comes in. Each DNS entry will now provide the CFS’s address and specific Resource Records.
Combining these three mechanisms, we obtain the following scenario. Imagine you’re the browser, and you want to make a request to “example.ch.” You head to your DNS resolver via DoH. The DNS informs you of the CFS’s location and associated Resource Records. From there, the browser constructs its ClientHelloInner, encapsulates it within the ClientHelloOuter, and sends the whole package to the CFS. The CFS possesses all the information needed to decrypt the ClientHelloInner. It then initiates a TCP transfer to the final destination. The latter recognizes the TLS and honors it, sending a response to the client, concluding the handshake. This entire process establishes a secure connection where only the CFS can identify the actual destination.
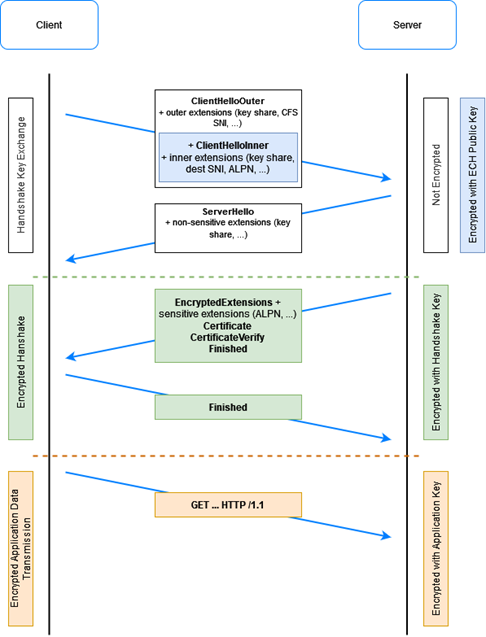
It’s essential to note that Encrypted Client Hello (ECH) is an extension of the TLS 1.3 protocol. This means it exclusively operates with this protocol version. If the server can’t support ECH, TLS 1.3 uses what’s called “Grease ECH,” a dummy version of ECH. In such cases, the browser will claim to use ECH even if it’s not supported.
This Encrypted Client Hello (ECH) represents a significant leap in TLS communication privacy, offering an elegant solution to safeguard user privacy.
ECH: A Clash Between Privacy and Security
The introduction of Encrypted Client Hello (ECH) in TLS 1.3 presents a complex interplay between privacy and security. Indeed, privacy demands security, but it often hesitates to share data with third parties for the sake of enhanced security. In the case of ECH, concealing the SNI can enhance privacy but might potentially compromise security. Striking a balance between these two needs is crucial. While ECH offers numerous privacy and security benefits, it also raises several challenges and concerns, which we will explore below.
Potential Use by Cybercriminals
ECH provides the ability to conceal the destination, raising concerns about its potential use by cybercriminals. Scenarios such as using ECH to hide the commands and control server of ransomware are worrisome.Impact on Security Products
The introduction of ECH has varying impacts on security products. Some, like domain name lookup blocking services, enterprise-managed devices, and browser security extensions, are minimally affected. However, products such as TLS proxy solutions, intrusion detection systems, and TLS proxy services are more heavily impacted.Compliance Challenges
End-to-end encryption as implemented by ECH, shields the entire communication, including the client hello and therefore the SNI, from external visibility. This approach complicates the task of selectively decrypting data for businesses that need to scrutinize traffic from suspicious sources or prevent the leakage of sensitive information. Indeed, filtering methods relying on the SNI are now ineffective, as the final destination of a communication remains unknown. As a result, these organizations may face substantial challenges in maintaining regulatory compliance, such as adhering to the stringent requirements outlined in the General Data Protection Regulation (GDPR), potentially incurring fines for non-compliance due to the inability to effectively monitor and filter encrypted traffic.Network and Education Security Challenges
The adoption of ECH poses challenges for network security, particularly in detecting threats from illegitimate addresses. Additionally, educational institutions and businesses may face difficulties in filtering and blocking access to inappropriate, violent, humiliating, suicidal, or pornographic content. These challenges can complicate the protection of children and online communities.
In summary, the introduction of Encrypted Client Hello (ECH) brings substantial privacy advantages but also raises complex issues related to security, regulatory compliance, and online content management. Seeking balanced solutions for these challenges is essential to ensure that ECH benefits all internet users.
The Underlying Political Implications of ECH
The introduction of Encrypted Client Hello (ECH) into the online security landscape has raised profound concerns regarding its political implications. This technological advancement undeniably has the potential to reshape the internet as we know it, with significant consequences for power dynamics and regulations. Let’s explore the key political implications.
Centralization of Power in Content Delivery Networks (CDNs)
Content Delivery Networks (CDNs) have drastically transformed the internet from an “end-to-end” model to an “Edge to Edge” paradigm. This shift has created a centralized gravitational effect within CDNs, primarily dominated by a major player, the United States. In other words, a considerable portion of internet traffic flows through the same CDN infrastructures, giving them a pivotal role in online content distribution.Reliability of DNS without DNSSEC
The first concern relates to using DNS to disseminate cryptographic session initiation data. The reliability of this approach is questioned as long as DNSSEC isn’t widely adopted. DNSSEC is a DNS extension designed to ensure the authenticity and integrity of DNS data. Without DNSSEC, there are risks of tampering and interception of DNS information. This is particularly relevant in censorship-prone nations, where governments can exploit these weaknesses to control or restrict access to websites that don’t align with their narrative.Economic Interests and CDN Market Dominance
Companies operating CDNs hold substantial economic interests as they significantly influence how internet traffic is routed. Their possession of sensitive information like the SNI grants them considerable power to implement security measures, but it can also hinder competition. This raises concerns about market dominance and CDN control over data flows.The Opaque Tunnel and Information Control
When an opaque tunnel is established between a user’s browser and web resources, a central actor wields significant control over what is visible, accessible, and concealed. This role will be assumed by CDNs which are mostly American and therefore subject to U.S. legislation. U.S. and European data protection and online security laws currently share some common ground, but future divergences are possible.
In summary, Encrypted Client Hello (ECH) goes beyond technical aspects and has profound political implications related to power centralization, competition, regulation, digital sovereignty, and privacy protection. Striking a balance between online security and safeguarding individual rights remains a major challenge in this ever-evolving landscape.
Adoption of ECH
Anticipating the potential adoption of Encrypted Client Hello (ECH) is a complex task, dependent on various factors, including its benefits and challenges. Below are some insights into future adoption.
Risks and Caution
The adoption of ECH could be limited due to associated risks and concerns. Privacy, security, and compliance issues may lead many stakeholders to approach ECH cautiously, restricting its deployment.TLS 1.3 Experience as a Benchmark
It’s essential to note that TLS 1.3 surpassed TLS 1.2 in adoption by demonstrating consistent growth over three years, eventually dominating after the fourth year. ECH may follow a similar trajectory if its advantages outweigh concerns.Substantial Support
The prospect of ECH ratification before summer 2024, as suggested by Arnaud Taddei, an IETF and World Telecoms Organization member, indicates significant support for this technology within the online security community.Early Adoption by Key Players
The fact that Chrome v117, Firefox v118 and CloudFlare are already in production with ECH is a positive sign. By July, Chrome had already reached over 1% ECH usage. These leading actors could influence others to adopt the technology, particularly if it demonstrates tangible benefits.
In the end, ECH adoption hinges on striking the right balance between its potential security and privacy advantages and implementation concerns. Close monitoring of its market evolution will be necessary to assess its long-term success.
