Introduction
On the afternoon of October 29, 2025 (UTC), Microsoft Azure suffered a major outage that rippled across the internet. Services from Microsoft Sentinel to Xbox Live and even some airline systems were impacted.
For many organisations, this was more than an inconvenience, it was a reminder that even the most robust cloud ecosystems can fail, and that availability incidents can easily be mistaken for security breaches.
In this post, we’ll walk through what happened, how it was mitigated, and what SOC teams should take away from the event.
What Actually Happened
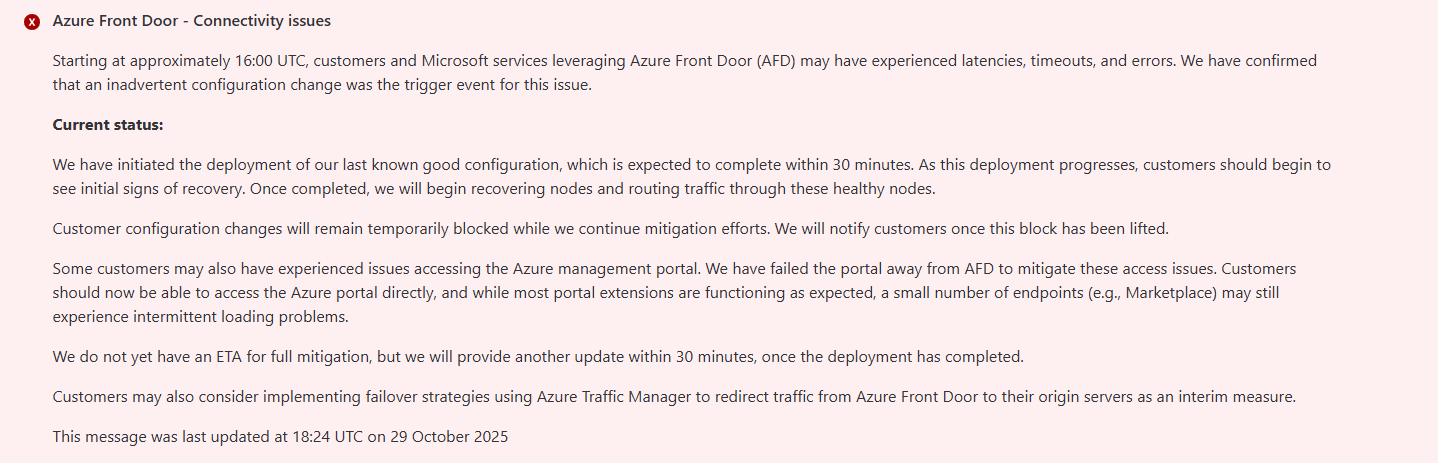
At around 16:00 UTC, Microsoft engineers noticed widespread latency and errors affecting customers using Azure Front Door (AFD), a global content delivery and routing service that sits between users and the cloud workloads they access. When AFD goes down, even perfectly healthy backend systems can suddenly appear offline.
Microsoft confirmed that the outage was triggered by an “inadvertent configuration change” that disrupted routing within AFD. In simpler terms, someone modified network settings that unintentionally caused Azure’s global front-end to stop handling requests correctly. The company quickly rolled back to a previous configuration and “failed the portal away from AFD” to restore access.
The impact was broad. Azure’s own portal became inaccessible, and services relying on AFD, including Xbox, Microsoft 365, and some airline booking systems like Alaska Airlines, experienced major slowdowns or outages. According to outage tracking site Downdetector, reports of Azure service failures peaked at more than 11,000 complaints globally.
Why This Matters for SOC Teams
At first glance, an event like this can trigger a flurry of alarms in SOC dashboards: authentication failures, API timeouts, and unusual error rates. To an analyst, this might look like a distributed denial-of-service attack or a major compromise.
The critical skill is differentiation, learning to tell the difference between an external outage and an internal security incident. Here’s how SOC teams can frame that reasoning:
- Correlation with Provider Status: Before escalating, check whether the problem aligns with known provider issues. If Microsoft’s own website is down, chances are the problem isn’t in your environment.
- Noise Reduction: Many alerting systems flood the SOC with “failed login” or “timeout” events when cloud dependencies fail. Tag and suppress these temporarily while maintaining visibility.
- Dependency Awareness: Map which internal services rely on Azure Front Door, CDN routing, or similar layers. That knowledge helps you assess impact quickly instead of treating every alert as unique.
- Clear Internal Communication: For business teams, what matters most is whether there’s been a breach. Early clarification that this is a provider availability issue can prevent panic and misinformation.
The Broader Picture
This incident is not the first of its kind. Azure experienced a smaller, region-specific Front Door disruption earlier this month. Each case underlines the same truth: in a cloud-first world, configuration is both a strength and a weakness.
When one misconfigured value can bring down half the internet, resilience depends as much on process discipline as on technical sophistication.
From a defensive standpoint, SOC teams can treat this outage as a live exercise. It’s a good opportunity to test alert suppression, provider monitoring integration, and internal communication workflows. Outages like this often expose weak points in how organisations interpret telemetry and coordinate incident response.
Conclusion
The October 29 Azure outage reminds us that cloud dependency comes with shared risk. Microsoft’s investigation shows no sign of a cyberattack, this was a human error propagated through global systems. Yet, the effect on customers was indistinguishable from a large-scale denial-of-service event.
For SOCs, the lesson is straightforward: not all red lights in your dashboard mean you’re under attack. Understanding upstream dependencies, maintaining calm under pressure, and integrating provider health checks into your monitoring stack are now essential parts of modern cyber defense.
When Microsoft releases its full post-incident report, teams should revisit this event, update internal playbooks, and simulate a similar failure to test readiness. The best time to prepare for the next outage is right after surviving the last one.
Sources
- The Verge – “A massive Microsoft Azure outage is taking down Xbox and 365”
- Reuters – “Alaska Airlines says website, app down amid global Azure outage”
- AP News – “Microsoft Azure cloud service hit with outage”
- Houston Chronicle – “AWS says it’s operating normally amid Microsoft Azure outage reports”
- Economic Times – “Azure down: Thousands of users complain about outage; here’s Microsoft’s latest statement”
