Industrial Environment Security
Challenges in OT Network Security
Industrial environments networks are often considered less secure than traditional IT environments. This is partly because OT systems were designed to operate autonomously with a focus on performance and real-time with less attention on security. Additionally, the equipment and communication protocols used in OT environments are often outdated and vulnerable to attacks.
Key Challenges
- Difficulty of updating equipment: Many industrial equipment are difficult to update due to their critical nature or very long lifecycle.
- Complexity of systems: Industrial systems are often complex and interconnected, making them difficult to manage and secure.
- Internal threats: Employees, subcontractors, or partners may access industrial systems and cause intentional or unintentional damage.
To enhance the security of industrial environments, it is important to have a secure-by-design approach, develop best practices for patching and coding, and have the capability to monitor and respond when an incident occurs.
Security by Design
The Purdue Model
The Purdue model was defined to establish best practices in terms of data separation between the OT and IT networks. It is based on a hierarchical architecture, dividing the information system into six different levels, each with its own security concerns and requirements.
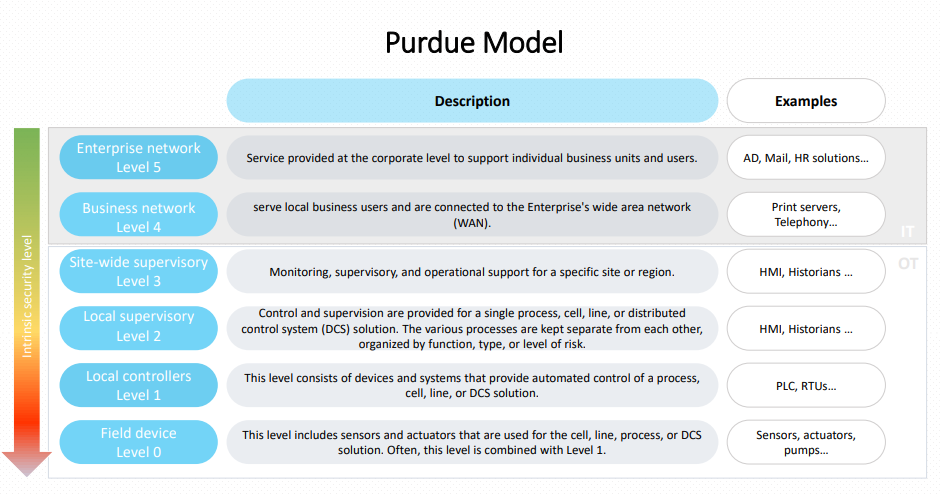
The Purdue model proposes a security architecture based on network segmentation into different security zones, including DMZ buffer zones, particularly between levels 3 and 4, where the industrial DMZ (level 3.5) is located.
Although debated in terms of modern relevance, especially with the rise of IoT, it remains a recognized standard and provides a solid foundation adaptable to industry-specific needs.
Segmentation
OT network segmentation is a vital security practice. It reduces the risk of attack propagation throughout the network.
Key principles:
- ICS protocols must remain confined to the control network (not above level 3).
- Lower layers, including the control level, must never have direct internet access.
Hardening and Patching
Hardening and patching are critical but challenging due to:
- Use of outdated and unsupported operating systems.
- Need to reduce attack surfaces via effective segmentation.
It’s also important to follow good coding practices, even for PLC programmers. A guide of the 20 best practices for coding PLCs, based on the OWASP Top 10 format, has been developed to ensure secure programming. The list of recommendations in detail can be found here.
Identification and Monitoring
Asset Identification
Understanding all assets is crucial. This includes:
- Identifying “crown jewels” (critical assets).
- Inventorying physical equipment, data flows, and networks.
Baseline
Defining a baseline enables anomaly detection:
- Data flows and configurations should be baselined.
- Example: A baseline could have prevented the Stuxnet attack.
Monitoring
Effective monitoring requires:
- Passive rather than active scans (to avoid disrupting sensitive equipment).
- Tools like Nozomi, Claroty, Microsoft Defender for IoT.
Key areas of focus:
- Remote connections (RDP, VPN, TeamViewer…)
- Border elements between IT and OT (e.g., data historian)
- Collecting logs and sending to a SIEM for early detection
Incident Response
A dedicated, trained incident response team is essential. They should:
- Understand ICS processes
- Maintain regular contact with operational staff
- Be ready to minimize operational impact and downtime during incidents
ICS Cyber Kill Chain
The ICS Cyber Kill Chain is a model from SANS Institute to understand and counter ICS-targeted attacks. It consists of two phases:
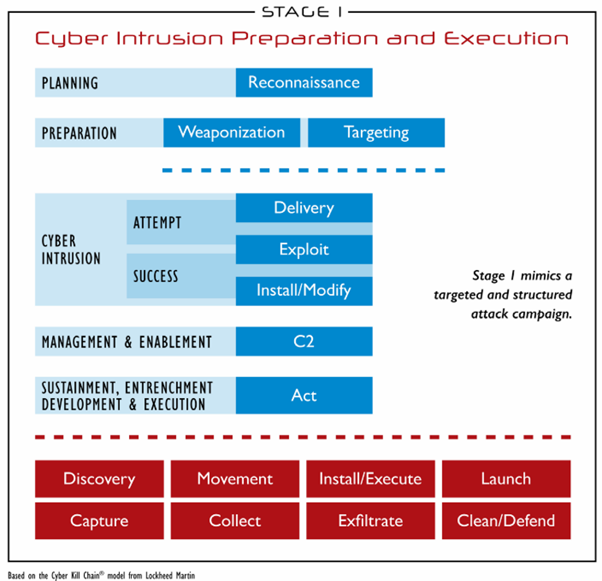
Phase 1: Intrusion & Learning
- Reconnaissance: Identifying vulnerabilities and entry points
- Delivery: Deploying malware (e.g., phishing)
- Exploitation: Using vulnerabilities to penetrate the system
- Installation: Installing malware to gain remote control
Phase 2: Attack
- Privilege Escalation: Gaining elevated privileges
- Propagation: Spreading across other ICS systems
- Malicious Act: Disruptions, parameter changes, or ransomware
Examples
- Stuxnet: Passed through all Purdue levels to reach nuclear centrifuges at level 0.
- Havex: A RAT used in espionage campaigns; introduced via phishing and watering hole attacks.
